If you experience any difficulty in accessing content on our website, please contact us at 1-866-333-8917 or email us at support@chicagovps.net and we will make every effort to assist you.
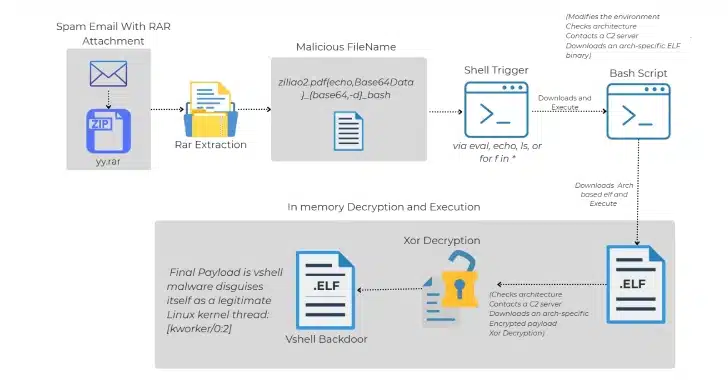
Cybersecurity researchers have recently identified a unique attack chain that employs phishing emails to distribute an open-source backdoor known as VShell. The attack begins with a spam email containing a malicious RAR archive file. According to Trellix researcher Sagar Bade, the novel malware infection process relies on the encoding of the payload directly in the filename instead of within the file content itself.
In this method, the attackers use shell command injection and Base64-encoded Bash payloads, transforming a standard file listing operation into an automatic trigger for malware execution. This technique exploits a common scenario in shell scripts where file names are handled with inadequate sanitization, allowing relatively harmless commands like eval or echo to unintentionally execute arbitrary code.
Moreover, traditional antivirus solutions often overlook this type of malware because they do not typically scan file names. The attack starts with an email that includes a seemingly innocuous RAR file. Within this file, there’s a specially crafted filename: "ziliao2.pdf{echo,<Base64-encoded command>}|{base64,-d}|bash`". When interpreted by the shell, this filename executes commands; however, execution only occurs when a command or script parses the filename, not just by extracting the file.
It’s important to note that manually creating such a filename isn’t feasible, suggesting it was either generated by a different programming language or dropped by a tool that circumvents normal shell input validation. The resulting execution leads to the triggering of a Base64-encoded downloader that later retrieves an appropriate ELF binary for the system architecture (such as x86_64 or armv7l), which then connects with a command-and-control (C2) server to download the encrypted VShell payload, decode it, and execute it on the host machine.
The phishing emails have been designed to resemble invitations for beauty product surveys, enticing recipients with a promise of rewards for their participation. Interestingly, although the email features a RAR attachment ("yy.rar"), it doesn’t explicitly instruct users to open it. This subtlety diverts the users’ attention from potential risk, as they may mistakenly assume it correlates with the survey.
VShell, a Go-based remote access tool, has seen significant use among Chinese hacking groups, including UNC5174, offering functionalities such as reverse shell access, file management, and encrypted command and control communications. What makes this attack particularly concerning is that VShell executes entirely in memory, thus evading detection by conventional disk-based security measures and is capable of targeting a wide array of Linux devices.
The analysis from Trellix underscores a concerning evolution within Linux malware delivery, where a mere file name in a RAR archive can be weaponized to execute arbitrary commands. This attack vector highlights the exploitation of command injections in shell loops as well as the misuse of the lenient execution environment of Linux, ultimately delivering a robust backdoor with comprehensive control over the targeted system.
Additionally, a concurrent analysis by Picus Security has revealed a new Linux-focused post-exploitation tool called RingReaper, which utilizes the Linux kernel’s io_uring framework to bypass conventional detection methods, although the identities behind these malware developments remain unknown.
ChicagoVPS is your gateway to unparalleled hosting solutions. Our state-of-the-art datacenters and powerful network ensures lightning-fast speeds and uninterrupted connectivity for your websites and applications. Whether you’re a startup looking for scalable resources or an enterprise in need of enterprise-grade hosting, our range of plans and customizable solutions guarantee a perfect fit. Trust in ChicagoVPS to deliver excellence, combining unmatched reliability and top-tier support.
For Inquiries or to receive a personalized quote, please reach out to us through our contact form here or email us at sales@chicagovps.net.
